Microsoft Sentinel SIEM
Microsoft Sentinel is a security information and event management (SIEM) platform that can be used to monitor Bitwarden organizations. Organizations can monitor event activity with the Bitwarden Event Logs app on Microsoft Sentinel.
Setup
To setup the Bitwarden integration, an active Azure account with access to a Microsoft Sentinel Workspace is required. Additionally, a Bitwarden API key, which can only be retrieved by organization owners.
Install the Bitwarden app to your Microsoft Sentinel dashboard
The Bitwarden Event Logs application can be located in the Microsoft Azure Marketplace. To add the new application to your Workspace:
Choose the Bitwarden Event Logs plan from the dropdown menu and select Create.

Bitwarden Event Logs marketplace app Complete the required fields and select the Workspace that will be monitoring Bitwarden organization data.
Once complete, select Review + create.
Connect your Bitwarden Organization
Once the Bitwarden Event Logs app has been added to your Microsoft Sentinel Workspace, you can connect your Bitwarden organization using your Bitwarden API key.
Return to the Data connectors screen and select the Bitwarden Event Logs app. Select Open connector page. If the Bitwarden Event Logs app is not visible, you may be required to select Refresh.

Microsoft Sentinel Bitwarden Event Logs app Keep this screen open, on another tab, log in to the Bitwarden web app and open the Admin Console using the product switcher:
Produktwechsler Navigate to your organization's Settings → Organization info screen and select the View API key button. You will be asked to re-enter your master password in order to access your API key information.
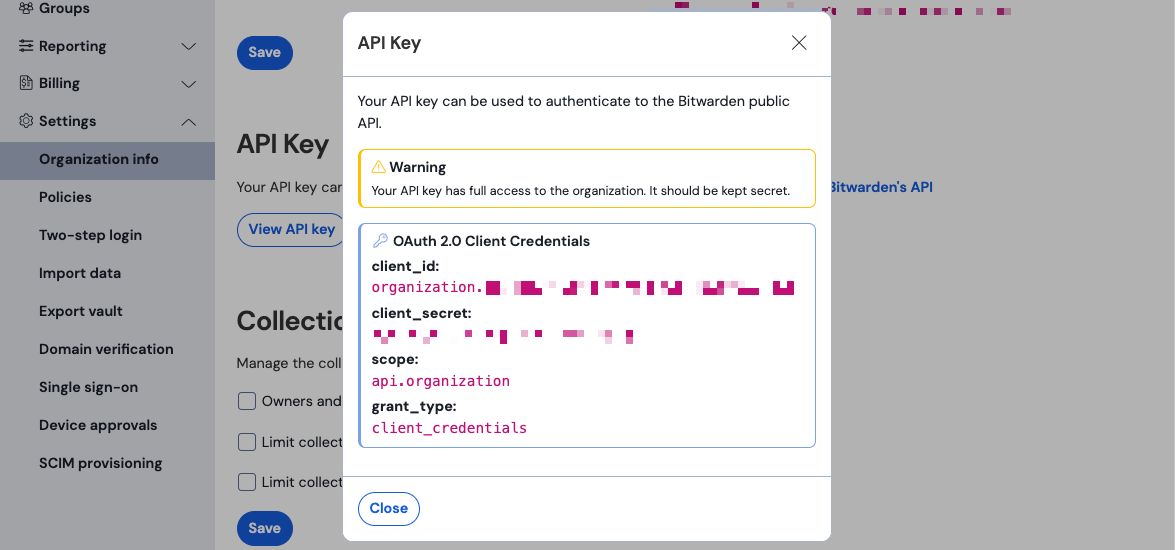
Organisation API Informationen Return to the Microsoft Sentinel tab. On the Configuration page, complete the following fields:
Field | Value |
|---|---|
Bitwarden Identity URL | For Bitwarden cloud users, the default URL will be For self-hosted Bitwarden users, input your self-hosted URL. For example, |
Bitwarden API URL | For Bitwarden cloud users, the default URL will be For self-hosted Bitwarden users, input your self-hosted URL. For example, |
Client ID | Input the value for |
Client Secret | Input the value for |
Select Connect once the required fields have been completed.
note
Die API-Schlüsselinformationen Ihrer Organisation sind sensible Daten. Teilen Sie diese Werte nicht an unsicheren Orten.
Start monitoring event logs
note
Historic event data is not available for the Bitwarden Event Logs app on Microsoft Sentinel at this time. Additionally, it may take up to 1 hour for the first events to appear in Microsoft Sentinel.
Bitwarden organization event logs can be viewed in Microsoft Sentinel using the BitwardenEventLogs query function.
From Microsoft Sentinel, select Logs. A New Query tab will be created. On the left hand navigation, select Functions → Workspace functions → BitwardenEventLogs.
Before running the query, you may select time frame and add specific parameters to the query. To being the query, select Run.

Microsoft Sentinel query Queries can be saved for future use.

Microsoft Sentinel query result
Monitor using Workbooks
Workbooks can be used to review event logs and visualize data. Additionally, templates are included in the Bitwarden Event Logs Workbook for a pre-configured overview of available data.
To access Workbooks, select Workbooks from the navigation and then Templates.
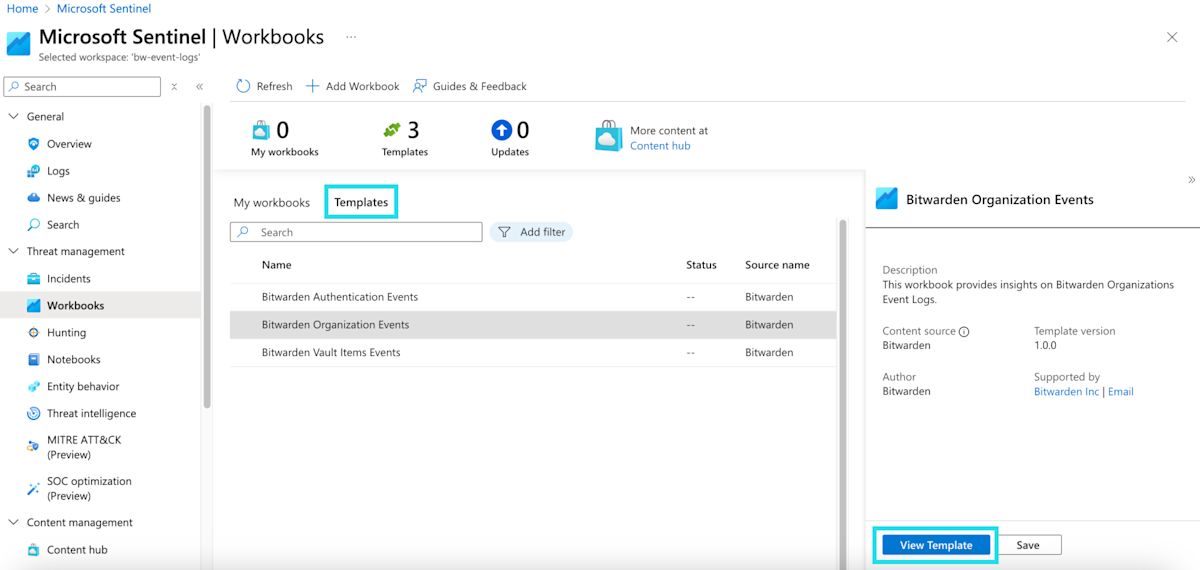
The Bitwarden Event Logs app will have three templates included by default. Select one of the templates and choose View Template to begin monitoring data.
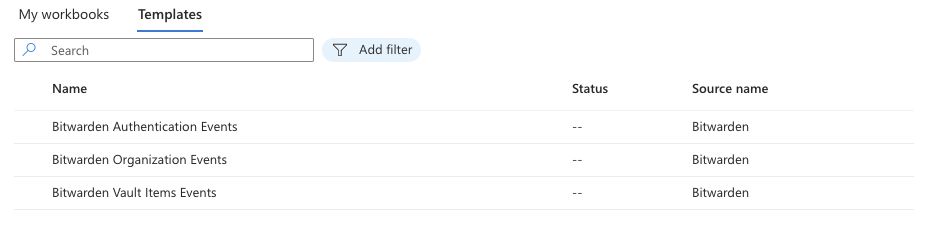
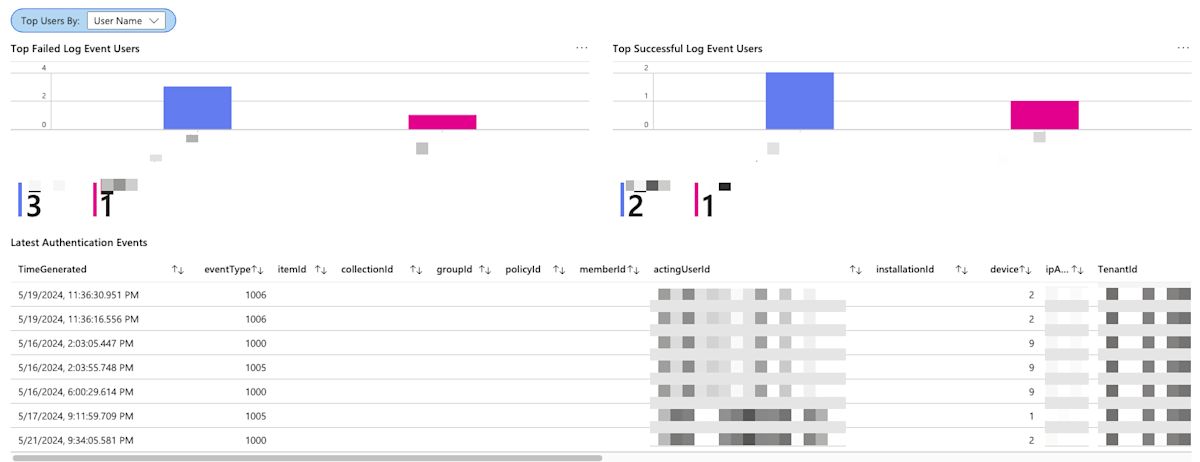
The dashboards include visualized data:
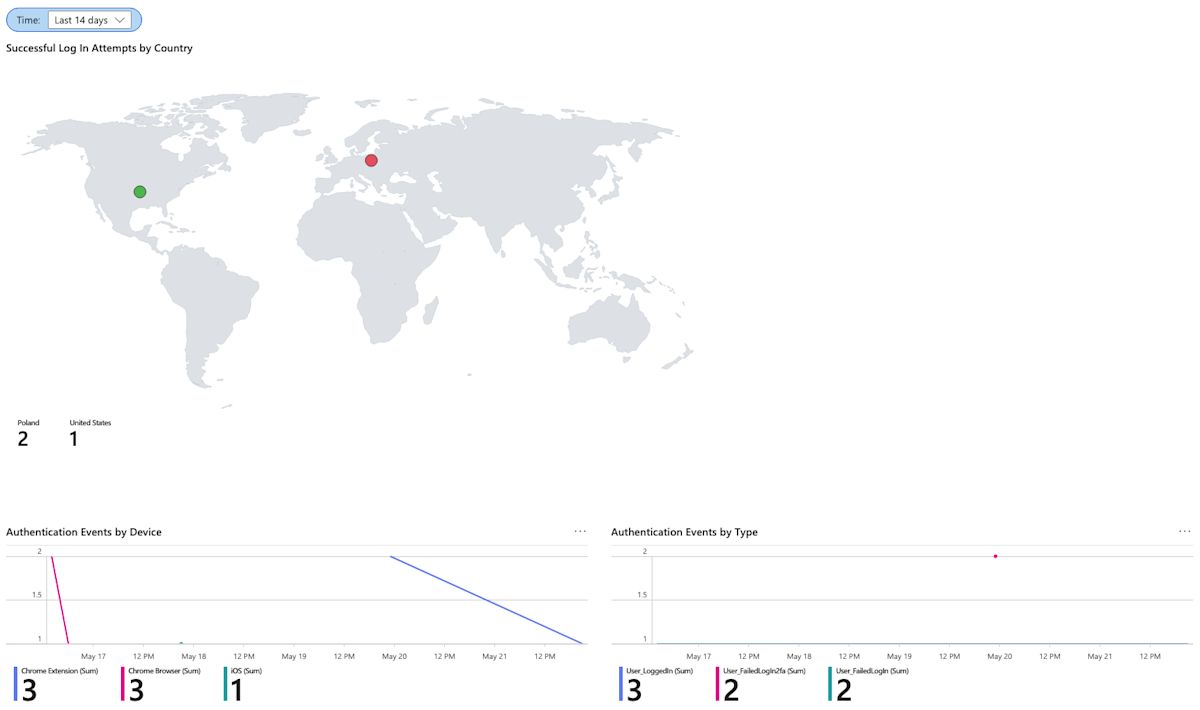
Continue scrolling the overview page for additional event log data: