Ping Identity SCIM Integration
System for cross-domain identity management (SCIM) can be used to automatically provision and de-provision members and groups in your Bitwarden organization.
note
Las integraciones SCIM están disponibles para organizaciones de Empresa. Las organizaciones de Equipos, o los clientes que no utilizan un proveedor de identidad compatible con SCIM, pueden considerar el uso de Conector de Directorio como un medio alternativo de aprovisionamiento.
This article will help you configure a SCIM integration with Ping Identity. Configuration involves working simultaneously with the Bitwarden web vault and Ping Identity Administrator dashboard. As you proceed, we recommend having both readily available and completing steps in the order they are documented.
Enable SCIM
note
¿Estás autoalojando Bitwarden? Si es así, complete estos pasos para habilitar SCIM para su servidor antes de continuar.
To start your SCIM integration, open the Admin Console and navigate to Settings → SCIM provisioning:
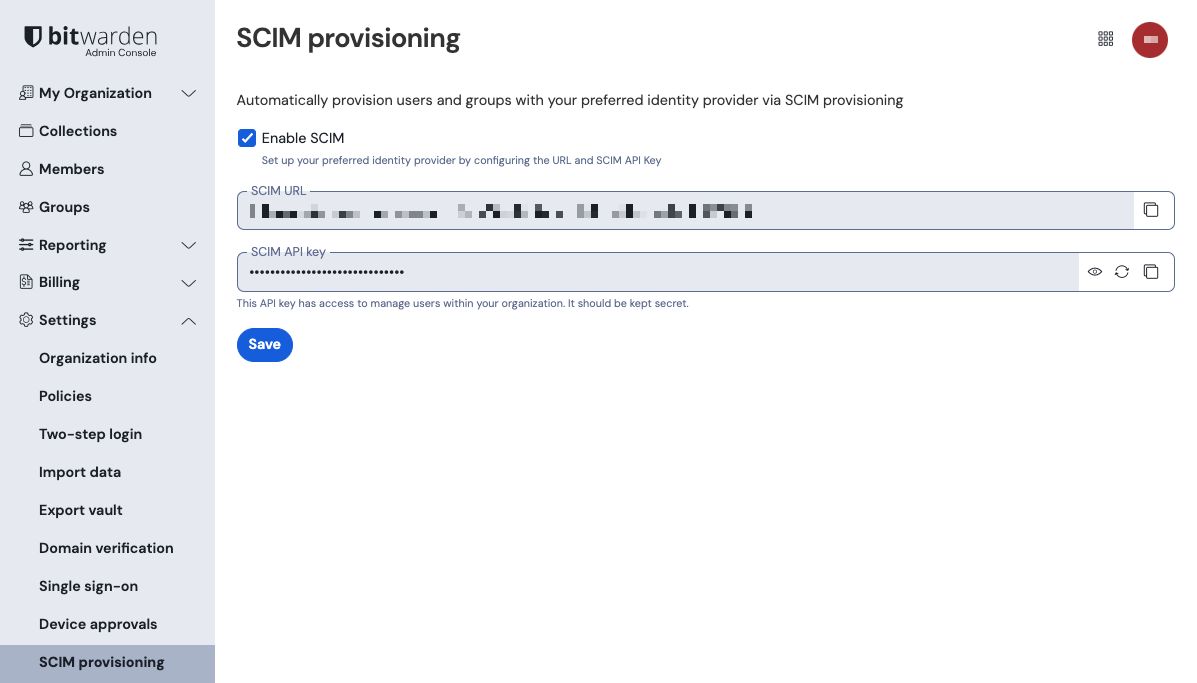
Select the Enable SCIM checkbox and take note of your SCIM URL and SCIM API Key. You will need to use both values in a later step.
Create a SCIM app
Navigate to provisioning New Connection.

Ping Identity new Connection In the Create a New Connection window, choose the Select option for Identity Store.
In the Identity Store, enter SCIM into the search box and select SCIM Outbound. Once this step is complete, select Next.

SCIM Connection Input a Name and Description for the SCIM connection.
Next, you will be required to input the SCIM BASE URL. Copy the SCIM URL value located on the Enable SCIM page in the Bitwarden Admin Console and paste it into this field.
Using the Authentication Method dropdown menu, select OAuth 2 Bearer Token. A field will appear named Oauth Access Token, paste the SCIM API key value from the Bitwarden Admin Console into this field.

Ping Identity SCIM connection test Once setup is complete, you may select Test Connection. If successful, select Next.
On the Configure Preferences page, select desired preferences and actions.
note
Setting the Remove Action setting to
Disablewill result in Bitwarden users being moved toRevokedstatus rather if the user fails to meet the filter criteria set on Ping Identity. Restoring the criteria will return the user to theirprevious state.
If the Remove Action is set toDelete, the same action will deprovision the user.Select Save once complete. Select the newly created Connection and enable the Connection using the toggle.

Enable Ping Identity Connection
Create a Rule
Before syncing user groups and directories, a Rule is required to sync the user groups to Bitwarden SCIM.
Return to the Provisioning Screen.
Select the Rules tab and then New Rule.
Enter an app specific name for the Rule and select Create Rule.
Edit the new Rule in the Configuration tab. Select Bitwarden SCIM connection and then Save.

Ping Identity Rule Select the Configuration tab and add a User Filter. For more information, see the Ping Identity documentation. Select Save once complete.

Ping Identity User Filter Enable the Rule using the toggle.

Ping Identity new Rule
Provision groups
To assign groups, return to the Provisioning screen and select the rule Edit Group Provisioning.

Edit group provisioning Choose the group or groups to provision and select Save. Once saved, the directory will trigger a sync.
Appendix
Required attributes
Both the Bitwarden and Ping Identity SCIM Provisioner with SAML (SCIM v2 Enterprise) applications use standard SCIM v2 attribute names. Bitwarden will use the following attributes:
User attributes
activeemailsª oruserNamedisplayNameexternalId
ª - Because SCIM allows users to have multiple email addresses expressed as an array of objects, Bitwarden will use the value of the object which contains "primary": true.
Group attributes
For each group, Bitwarden will use the following attributes:
displayName(required)membersªexternalId
ª - members is an array of objects, each object representing a user in that group.