- Blog
- Software supply chain security best practices
Top strategies for securing the software supply chain
As software becomes more integrated and reliant on various components and libraries, supply chain vulnerability and malware risk increases. Attackers are becoming more sophisticated, and development teams must implement a comprehensive software supply chain security strategy to protect the entire software lifecycle. This challenge is exacerbated by the fact that developers often vastly outnumber security experts, with some estimates showing a ratio of one DevSecOps engineer to 200 developers.
Let’s explore best practices for development and DevSecOps teams to enhance security.
Early software supply chain security integration
Emphasizing security from the start of the development process - sometimes labeled as shift left security - pushes for testing and security-focused processes starting earlier in the software development process, right where developers begin. Doing so reduces the number of mistakes that might propagate through to downstream stages of the development lifecycle. Ultimately, this reduces QA work and remediation costs.
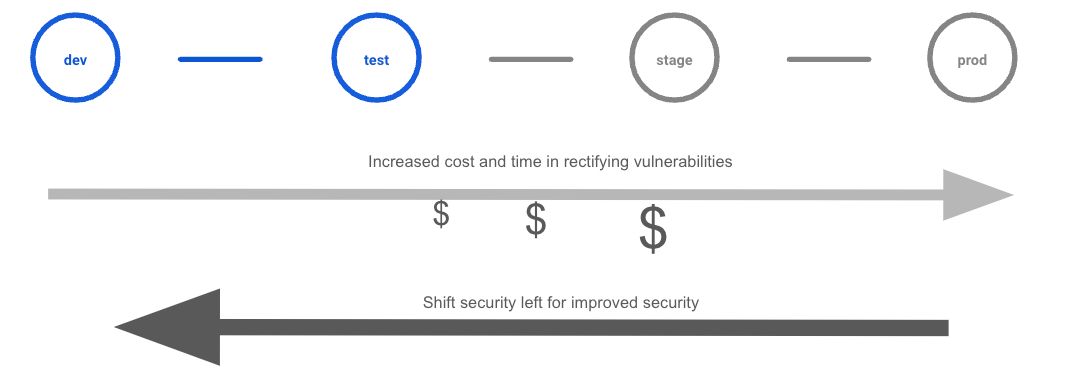
Examples of early software supply chain security integration might include practices such as Static Application Security Testing (SAST), dependency checking that seeks to identify vulnerable dependencies, centralized secrets management, and many more.
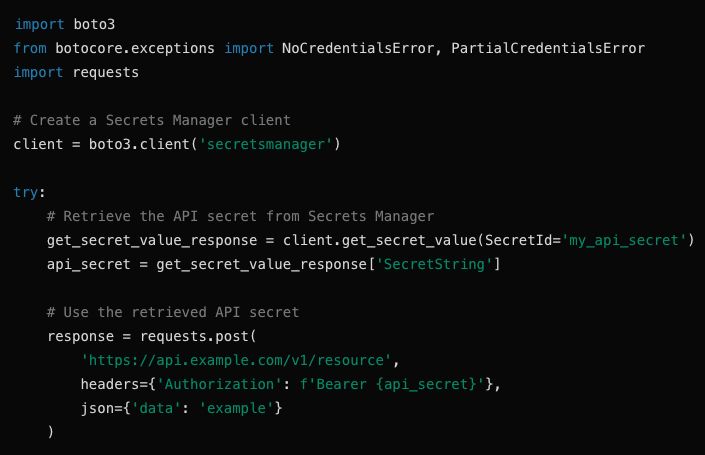
Managing secrets securely is crucial to provide a robust foundation for applications and teams, ensuring that sensitive information like machine secrets, API keys, tokens, and access credentials are secure and protected against unauthorized access and exposure. A secrets manager helps prevent unsafe practices like embedding secrets in code or sharing secrets across public channels like Slack along the development cycle.
Emphasizing SBOM
A Software Bill of Materials (SBOM) provides transparency and visibility into all software components, including third-party and open source libraries. This comprehensive view helps organizations swiftly identify and manage vulnerabilities, facilitating prompt remediation when new security flaws are discovered. SBOMs are also essential for compliance, helping meet regulatory requirements and industry standards such as GDPR and HIPAA.
Understanding software dependencies through an SBOM allows for better risk management by assessing and mitigating risks associated with third-party components. SBOMs enhance software supply chain security by offering a verifiable record of all components, aiding in the detection and prevention of software supply chain attacks. In the event of a security breach, an SBOM enables quicker and more effective incident response by pinpointing the affected components, allowing for targeted mitigation efforts.
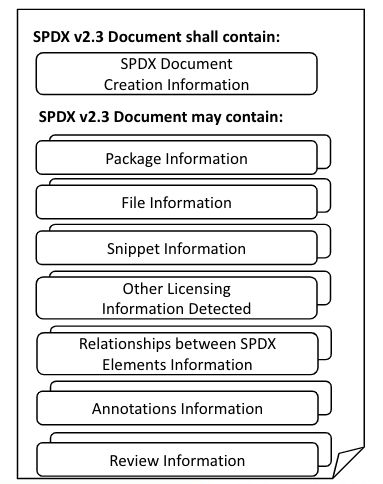
There are a number of open source tools that support the System Package Data Exchange standard (SPDX) and can help map relationships between components, and the association of security and licensing information with each component.
Automation and monitoring
Automated security testing and continuous monitoring identifies vulnerabilities, and aims to rectify them before they compound, maintaining a more secure software supply chain environment.
Automated security testing involves using tools to automatically scan code for security issues throughout the development lifecycle. Tools like SAST analyze source code for known vulnerabilities before compilation, and Dynamic Application Security Testing (DAST) tests running applications to identify vulnerabilities in real-time (eg. SQL injections, cross scripting), Integrating these tools into CI/CD pipelines ensures security checks are performed consistently.
Continuous monitoring tracks real-time application performance and security metrics to quickly detect and respond to potential threats. By employing open source monitoring and analytics tools like Prometheus and Grafana, organizations can collect, visualize, and alert on various metrics and logs from their applications and infrastructure. These tools help maintain an ongoing awareness of the system’s health and security posture, enabling rapid response to anomalies or breaches.

Collaboration, compliance, and culture
Collaboration: Effective integration among development, DevOps, and DevSecOps teams enhances software supply chain security. Development teams focus on writing secure code and conducting regular code reviews, using tools like SAST to identify vulnerabilities early. DevOps teams manage infrastructure, ensuring CI/CD pipelines include automated security checks and practices like Infrastructure as Code (IaC). DevSecOps teams integrate security into the DevOps workflow, implementing automated compliance checks, managing security incidents, and conducting regular assessments. Together, these roles ensure comprehensive software supply chain security from design to deployment.
Compliance: SBOM compliance, formalized by Executive Order 14028, aims to protect federal agencies from cybersecurity threats and software supply chain attacks. It involves creating an SBOM with each release, attesting to its accuracy, and sharing it with relevant entities, ensuring transparency and end-of-life tracking.
Culture: Fostering a security-first mindset through regular training and awareness programs is essential, promoting a culture where security is a shared responsibility. Security tasks should not be relegated solely to DevSecOps or DevOps but should be a comprehensive effort involving all teams. By aligning efforts and sharing responsibilities, these teams create a robust and secure software development lifecycle.
Secure your development and infrastructure secrets with Bitwarden Secrets Manager
Ready to get started on your secrets management journey? Choose the end-to-end encrypted and open source secrets manager trusted by teams and businesses of all sizes to secure their critical secrets, Bitwarden Secrets Manager.
Bitwarden Secrets Manager offers predictable pricing and unlimited secret storage on any plan. To test out all the business functionality that Bitwarden Secrets Manager has to offer, sign up for free or opt for a 7-day business trial to explore all the enterprise features Bitwarden Secrets Manager has to offer. You can also contact sales for a personalized consultation.
