- Blog
- Bitwarden security fundamentals and multifactor encryption
Security starts with your Bitwarden password
The password you use to log into your Bitwarden account plays a central role in protecting your vault by enabling encryption and decryption. In a recent video, Tom Lawrence of Lawrence Technology Services discussed the importance of “high entropy master passwords.” In plain language, this means a master password with an uncommon combination of characters and words that are long and complex.

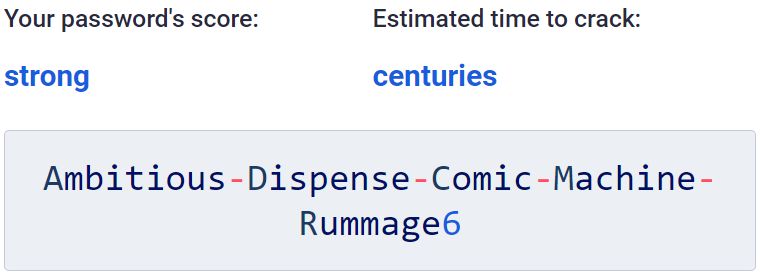
Password entropy makes it harder for malicious actors to guess your password and gain access into your vault by making it significantly harder and processing-intensive for a computer to guess. In short, “having a good master password increases entropy exponentially” – and therefore the impracticality of cracking the master password that encrypts your vault.
Multifactor encryption reinforces security
Your vault is encrypted starting with the master password along with your email address. A strong master password provides the first and most important level of protection. Beyond this, Bitwarden adds additional layers of encryption and protection – called multifactor encryption – when your vault is stored in the Bitwarden cloud. This makes it practically impossible for a bad actor to break into your vault, even if they were able to gain access to your encrypted vault data.
Encryption for data in the cloud
When using the Bitwarden cloud, your vault data is stored on secure cloud servers to provide convenient access to your vault on all of your devices. Your encrypted vault is protected with multiple factors and layers of encryption stacked atop the existing encryption enacted by your master password.
The Bitwarden cloud database stores your encrypted vault and is hosted within the secure Microsoft Azure cloud infrastructure. It is configured with an encryption-at-rest technology provided by Azure called Transparent Data Encryption (TDE). TDE performs real-time encryption and decryption of the entire Bitwarden cloud database, associated backup data, and transaction log files when they’re not in-use. Azure handles the encryption keys for TDE, which only authorized Bitwarden server components are able to access. Read more about Azure’s Transparent Data Encryption here.
Additionally, Bitwarden server applications perform their own encryption of sensitive database columns related to your user account. Master password hashes and protected user keys are encrypted on the fly as they move in and out of the Bitwarden cloud database. These column-level encryption operations are performed with keys that Bitwarden manages in a strictly controlled key management service (KMS).
Guarding the Bitwarden cloud infrastructure is a robust cloud operations team, which monitors web traffic, malicious activity, and perimeter strength. The team also ensures high performance and uptime of the platform.
Encryption for data in transit
When transmitting vault data, Bitwarden uses Transport Layer Security (TLS), a standard encryption protocol that most websites and web services use today, including banks, universities, telecommunications applications, and more. This secure communication between computers stops third parties from intercepting information across the connection.
An authentication hash, derived from your email address and master password, ensures Bitwarden sends the encrypted vault to the right device. The authentication hash is generated on your device and securely sent to the server, which compares it to the encrypted record on file. Only if entries match will the encrypted vault be sent to your device.
As a complement to encryption, Bitwarden offers two-step login, also known as 2FA or MFA, to protect your account. With two-step login turned on, the Bitwarden server will ask you to prove who you are through a different form of authentication – for example, a hardware key, authenticator code, or email verification.
Vault encryption and the key derivation function
Your Bitwarden vault is encrypted using complex cryptographic algorithms and locked up tight. Your master password is used to derive a master key, which is the only thing that can open your vault. The master key is generated by a key derivation function (KDF) using your master password and email address as inputs when you log in to Bitwarden. The master key never leaves your device and is deleted when you lock or log out of your vault.
The key derivation function is a specialized computer algorithm that creates a long string of characters (the key) from your email address and master password. The result from the KDF algorithm gets fed back into itself many times, known as KDF iterations, before arriving at the master key. This process is complex, but not random, and will always give the same result with the same inputs and settings.
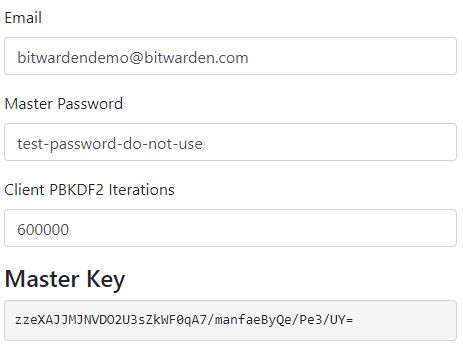
How the key derivation function protects your vault
The key derivation function plays two roles. First, it creates a master key from your email address and master password suitable for encryption purposes. Second, it imposes a processing speed bump for anyone trying to crack into your vault. With a strong master password, a hacker would have to make billions or trillions of password guesses to try to get into your vault, and every KDF iteration multiplies the amount of processing power and time required to make those guesses.
As of early 2023, OWASP recommends 600,000 iterations for the PBKDF2 key derivation function. Bitwarden users have always had the option to specify the number of iterations for their account, and 600,000 is now the default value for new accounts. Bitwarden has also recently added another KDF option called Argon2id, which defends against GPU-based and side-channel attacks by increasing the memory needed to guess a master password input.
Instructions on how to update KDF iterations are here, and remember that it is always good to have an export of your vault before making any settings changes to cryptographic operations. Regardless of the iteration count, a strong master password is always the best way to protect your vault data.
“If your password is bad, your likelihood of being secure is bad. It doesn’t matter how many iterations you have.”
Tom Lawrence, infosecurity expert
A comprehensive approach to encryption
The Bitwarden security strategy protects your vault data with several layers of encryption and protection, each layer providing extra defenses against malicious actors. Rounding this out are multifactor authentication options, core to identity and access procedures. This approach ensures that your data is secure as it moves from one location to another – from your device to the Bitwarden servers and vice versa, in-transit and at-rest. With Bitwarden zero knowledge end-to-end encryption, your sensitive data is protected with a highly effective defense in today's cybersecurity environment.
Resources
Learn more about creating a strong master password in this blog article.
Read the help article on encryption, or the Bitwarden Security Whitepaper.
Check out the Password Strength Testing Tool and the Strong Password Generator for help in creating strong passwords.
Visit bitwarden.com today to learn more about password management, plans, pricing, and how Bitwarden can help you keep your logins and other sensitive data secure!