- Blog
- How to identify a phishing attack
Any internet user can be the target of a phishing attack. This blog will define phishing, discuss recent statistics pertinent to understanding how a phishing attack might play out, share tips to help identify a phishing attack, and end with some strategies for protecting data - such as utilizing a password manager.
What is a phishing scam?
Phishing consists of fake reach-outs that seek to exploit users’ fears, curiosity, or helpfulness, often with an element of urgency intended to prompt an immediate interaction. Phishing operations seek to compel people to divulge personally identifiable information (PII) such as passwords, financial information, or social security numbers. Some operations may drive people to click on websites containing malware so cyber criminals can infect computers and steal even more sensitive data, sometimes with the goal of engaging in identity theft.
A particularly dangerous attack is called spear phishing, which involves highly personalized messages targeting specific individuals or organizations.
Check out this ebook by hacker Rachel Tobac to learn more about how to stay safe online.
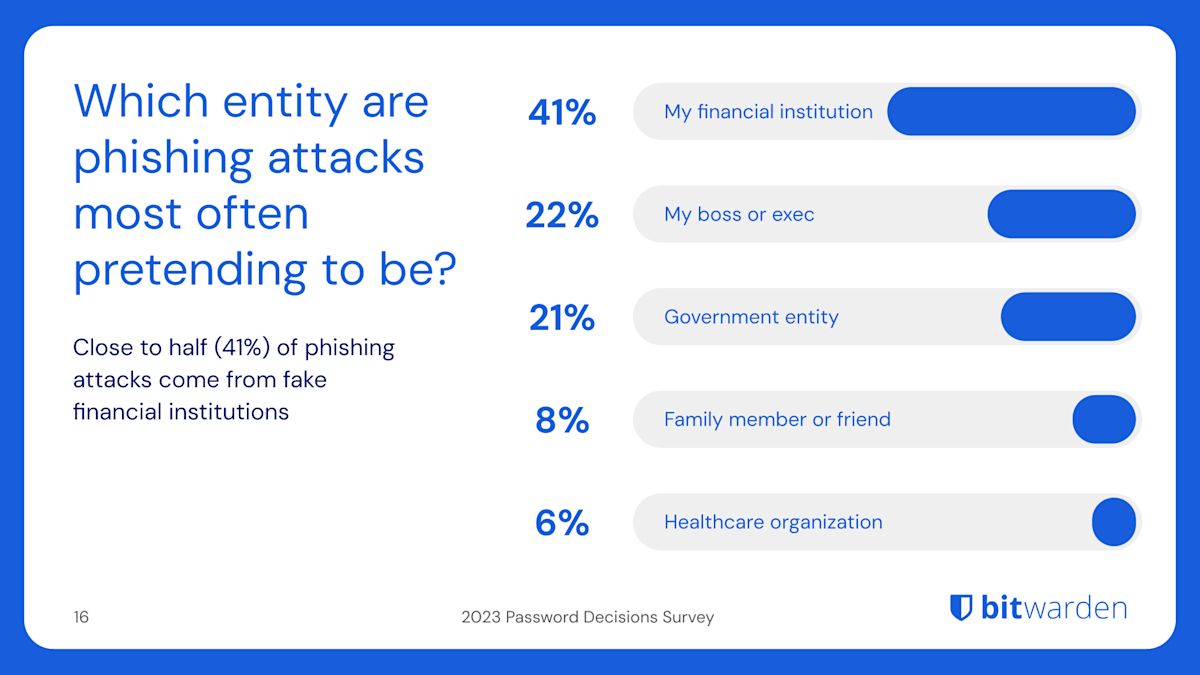
Phishing operations often mask their malicious intent by posing as reputable institutions. According to the Bitwarden Password Decisions Survey, nearly half (41%) of phishing attacks come from fake financial institutions, 22% from purported bosses or executives, and 21% from fake government agencies.
How to identify phishing emails
Note: Bitwarden will never ask you for your master password via email or any other method.
While phishing attacks are unfortunately increasingly sophisticated, there are still some tell-tale signs that an email or attachment may be part of a phishing scam.
To start with, phishing-oriented emails purporting to come from reputable institutions might show a suspicious email sender’s name and email address. For example, an email supposedly from Chase Bank could be missing a letter or include a random symbol (@chas.com), indicating the sender may be attempting a phishing attack.
Links purportedly sending you to the IRS, DMV, or Amazon may also be problematic. It’s worth taking an extra few seconds to hover over links to confirm they go to the proper website. If unsure, log in to the account directly or pick up the phone and speak with an official customer service representative to verify the correspondence is legitimate.
Avoid opening attachments from people you don’t know. Receiving unexpected attachments from names you don’t recognize is a sign the sender may be trying to scam you, engage in identity theft, or entice you to download malware.
Another telltale sign is correspondence riddled with spelling and grammatical errors, messages that claim there’s a problem you need to urgently address, and messages alerting you to “suspicious activity.” However, these spelling errors will likely become less common as generative AI spreads.
For a more exhaustive list of signs, see the Federal Trade Commission (FTC) informative web page devoted to spotting a phishing attack.
Among other insights, the FTC notes: “While real companies might communicate with you by email, legitimate companies won’t email or text with a link to update your payment information. Phishing emails can often have real consequences for people who give scammers their information, including identity theft. And they might harm the reputation of the companies they’re spoofing.”
Common indicators of phishing attempts
Phishing attempts often exhibit certain characteristics that can help identify them. Threatening language designed to create a sense of urgency or fear and pressure someone into acting immediately is a common indicator of a phishing attack. Pay close attention to grammar and spelling; many phishing emails will contain noticeable spelling and grammatical errors. Generic greetings like “Dear Customer,” instead of an individual’s name, are another red flag to watch out for.
Keep an eye out for suspicious URLs or domain names. Be sure to hover over links to see the actual URL, and look for any discrepancies with unusual or mismatched email domain names. Phishers often create URLs that look similar to legitimate ones but with slight misspellings or added characters, so it’s crucial to always double-check the domain name to ensure it matches the legitimate company’s domain. Note also that even URLs that use HTTPS should not necessarily be trusted - while HTTPS indicates a secure connection, it does not guarantee the legitimacy of the website. A password manager can help flag lookalike sites. When a user is on a login page that does not match the URL stored with the intended account, the password manager will not autofill the credentials, giving the user a chance to double-check the validity of the website.
Be wary of unexpected links or attachments, especially from unknown senders. It is also important to be cautious with requests for personal or financial information; legitimate companies will rarely ask for sensitive information via email or text.
Recognizing these signs can help you avoid phishing scams and protect your personal and financial information.
Protecting sensitive information from a phishing attack
The FTC provides four solid recommendations for protecting data from a phishing attack. They include:
Use security software to protect your computer and remember to run software updates.
Protect your mobile phone by setting software to update automatically.
Leverage multi-factor authentication, also known as two-factor authentication and two-step login, for an extra layer of protection in the event a cyber-criminal gets a hold of your login credentials.
Back up computer data to a hard drive or the cloud and back up mobile phone data.
Report phishing attempts to organizations such as the Anti-Phishing Working Group (APWG) to help mitigate their occurrence.
Password managers are also a very important tool for protecting against phishing. They help users keep track of website URLs, retain known and confirmed URLs, and confirm when a user is landing on a known site. All this is in addition to their primary, fundamental mission of enabling users to generate, store, and secure strong and unique passwords in an end-to-end encrypted vault.
Get started with Bitwarden
Ready to level up your cybersecurity with Bitwarden? Sign up today for a free Bitwarden account, or start a 7-day free trial of our business plans so your team and company colleagues can stay safe online. Still have questions? Check out the live weekly demo to speak directly with the Bitwarden team.