AI has unlocked a world of new innovations and unexplored opportunities for businesses. But balancing the potential of AI and all of its innovations with the need for security can often feel daunting.
The challenge is compounded because companies often lack strong internal protections (1) and many have failed to make cybersecurity training and education a cultural priority in the workplace. A recent Bitwarden survey of more than 600 IT developers found that 68% of respondents rate continuous security training as “extremely important,” yet close to half (43%) undergo security training only once a year or less.
A recent Bitwarden survey of 710 data security professionals in over 30 industries in North America, along with prior Bitwarden research (such as the 2023 password decisions survey), and eye-opening business press reports, reveal how the use of AI has exposed companies to potential threat vectors and opportunities for bad actors to access sensitive information. (2) Security professionals need to stay ahead of this complex but important concern. To ensure data security while leveraging the potential of AI, companies can benefit from:
Evaluating how their data will be used before investing in AI software and data-security solutions
Regularly inspecting the nuts and bolts of their new and existing AI software for any vulnerabilities
Leveraging trusted cybersecurity solutions to safeguard business accounts and securely store sensitive information
This eBook reveals the recent survey findings to help security professionals ensure their organizations remain innovative while keeping their data safe. The results of this research shed meaningful light on:
The cybersecurity overconfidence gap
The evolving role of AI in cybersecurity
What organizations can do to safeguard sensitive data
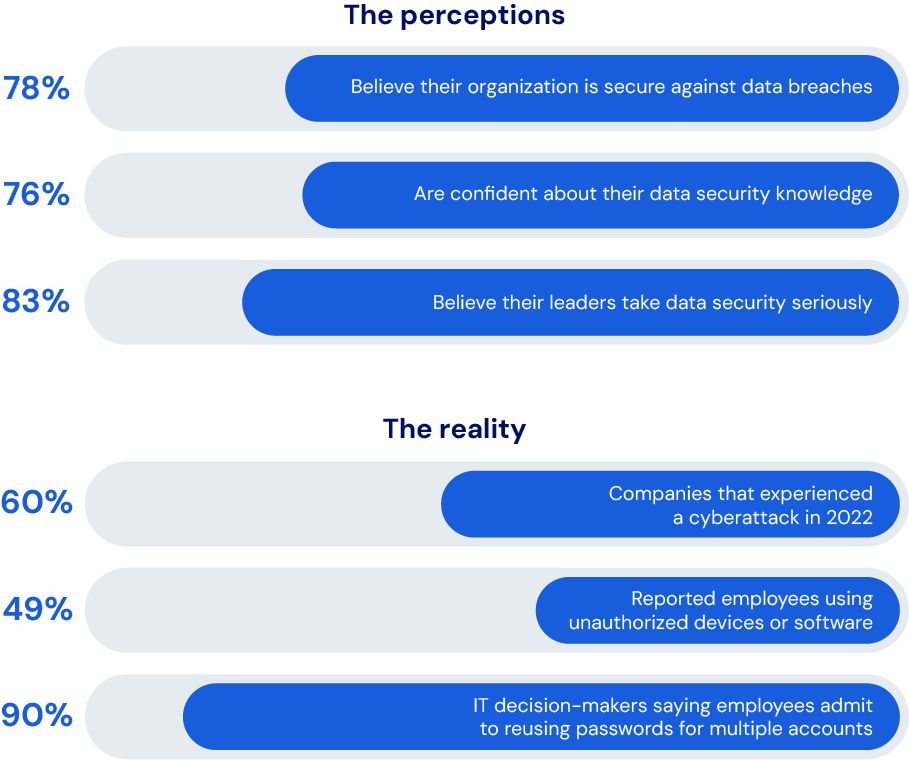
The cybersecurity overconfidence gap
The first step toward strengthening the security of privileged business information is evaluating the gap between the confidence among IT decision-makers to ward off cybersecurity risks and the actual threat that AI poses to cybersecurity.
The takeaway: Although a large majority of IT decision-makers believe their organization is secure against data breaches, they also report rampant use of potentially harmful IT practices.
What the research shows is that while employees might feel comfortable with their data security practices, companies are likely to be facing unrealized vulnerabilities that are creating risks to their businesses.
Graph source: Survey Findings: Balancing Security and Innovation in the Age of AI and 2023 Password Decision Survey
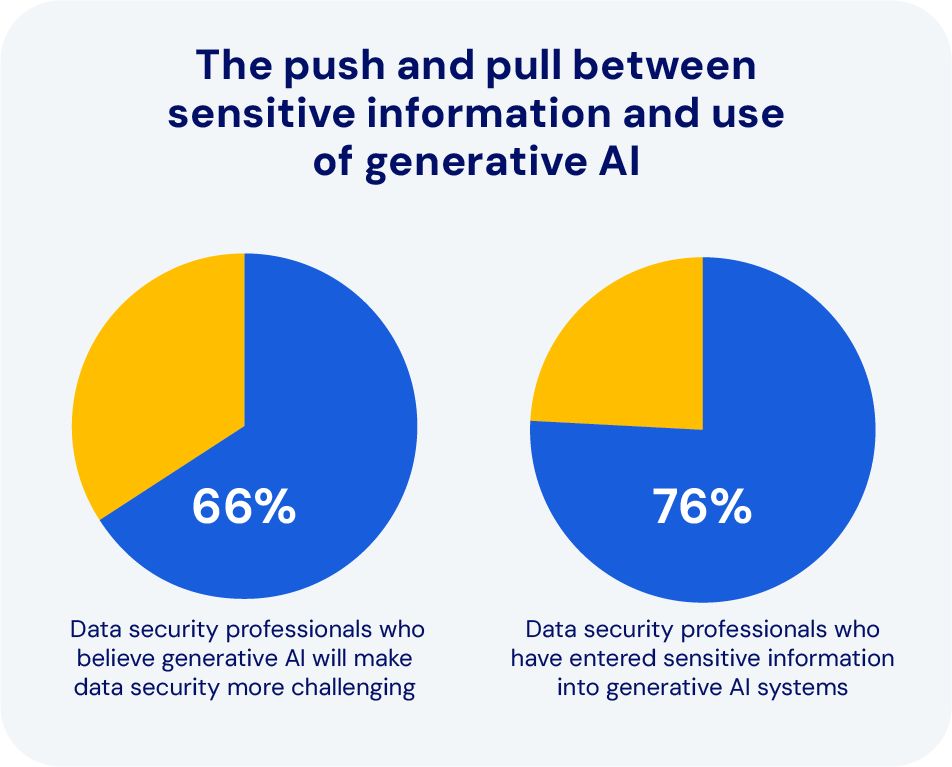
The evolving role of AI in cybersecurity
With AI becoming mainstream, we see the new risks in the security environment already facing serious challenges. The challenges are heightened by the rapid increase in AI use overall and the increased dependency in the workplace on AI technology. The Wall Street Journal reports that “companies are drowning in too much AI,” largely because IT vendors “are rolling out an avalanche of new generative AI features.” (3)
The takeaway: Although most data security professionals feel AI will make their responsibilities more difficult, both they and business leaders are entering sensitive information into generative AI systems.
A major concern is that as companies share more data through interconnected networks, the possibility of a breach or damage due to AI increases, with potentially significant consequences for the business.
Other trends also raise the possible threat of AI to cybersecurity, including:
Increased centralization of business data
Weak links in AI networks
The duplication of data within AI programs
Insider threats (employee misconduct, either intentionally or accidentally)
Graph source: Survey Findings: Balancing Security and Innovation in the Age of AI
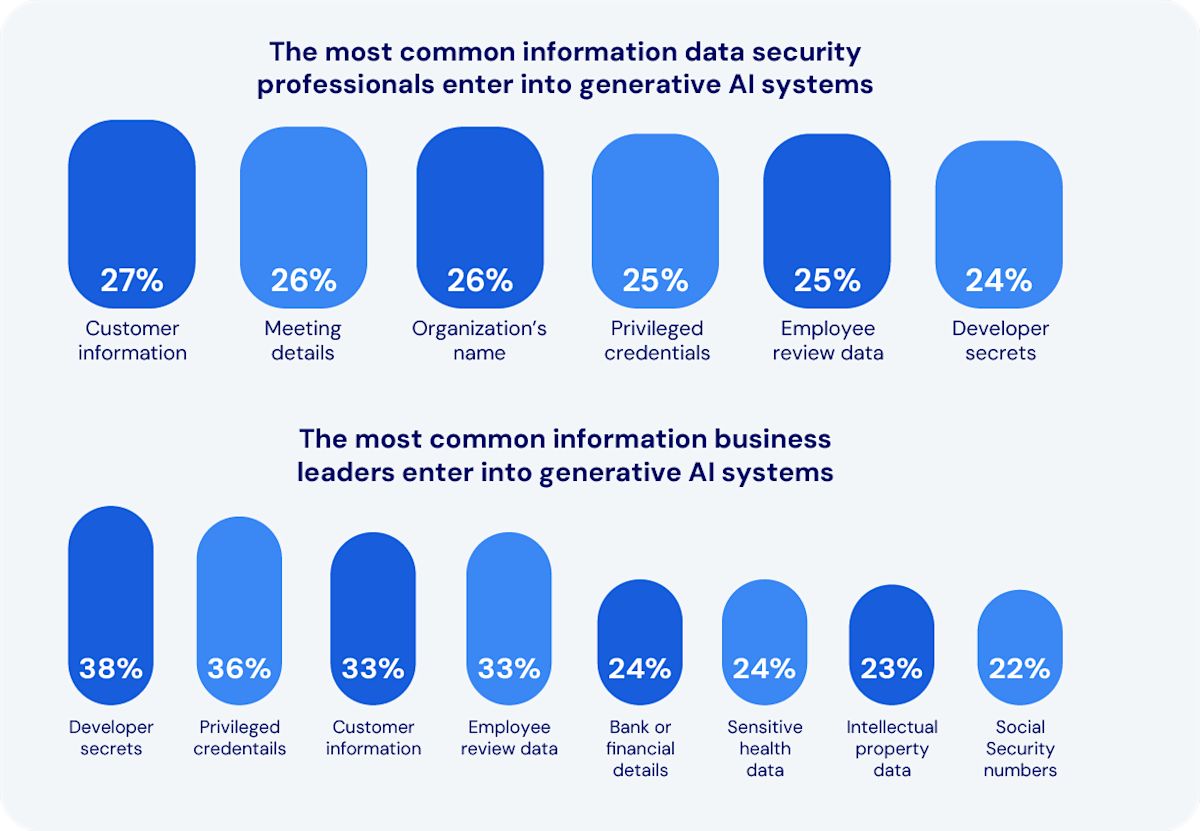
However, as much as AI poses a serious threat to cybersecurity, that threat remains largely speculative. (4) Most proven security breaches related to AI have been the result of hackers using it to scam consumers or steal personal information from businesses. Even then, the threats get more attention than any actual attacks or breaches.
Abnormal Security has reported on hackers using generative AI to produce convincing internal and external emails to trick recipients into sharing personal information, access credentials, and financial information.(5)
Reuters cites cybersecurity experts claiming hackers are using AI in sophisticated phishing attacks (6) (but did not provide any specific incidents).
Infosecurity reports hackers have used AI to program keystroke monitoring for malware and ransomware. (7) Again, no specific instances were cited.
Graph source: Survey Findings: Balancing Security and Innovation in the Age of AI
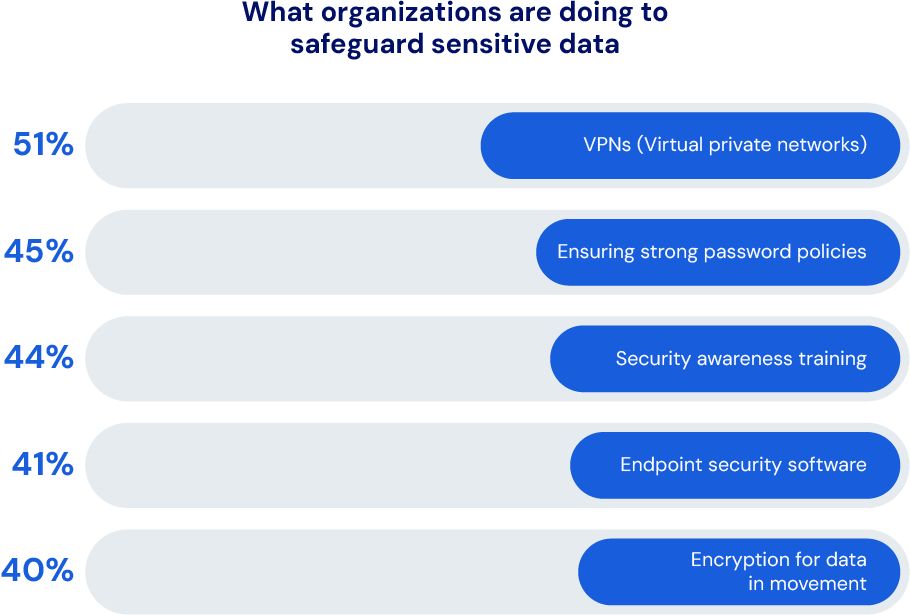
What organizations can do to safeguard sensitive data
As companies continue to develop and implement AI systems, it’s more critical than ever to ensure that the technology and the data it holds is properly secured. This is essential to prevent data breaches that can result in legal liability, harm to the company’s brand, hefty fines, and significant financial loss.
The best approach is for security and IT professionals to be proactive. This way, businesses can strengthen their defense mechanisms against cyber threats and ensure data safety.
Graph source: Survey Findings: Balancing Security and Innovation in the Age of AI
But how effective are these measures?
In reality, a VPN may not help deter irresponsible behavior involving generative AI. VPNs are a good network security measure when people are accessing networks remotely. But its value in preventing security breaches is passive rather than proactive. For example, if a customer’s data is part of a phishing attack that is gathered from an AI tool, a VPN wouldn't protect them.
Security training should be considered and activated to prevent data lapses of all kinds, including AI-generated data. Strong password policies are also a meaningful deterrent and can be used downstream if someone's data is compromised.
In fact, user education, tools, and training are critical for ensuring employees have the most up-to-date knowledge and skills to prevent data breaches as the use of AI systems proliferates. Practices that are successful include:
Ensuring end-to-end encryption of sensitive information on any employee device or platform (regardless of whether they’re working in the main office, at a remote location, or on the go).
Sharing sensitive information securely with internal and external parties, based on protocols that employees have been trained on.
Centralizing IT security policies and management of user access, so all employees have easy access to the most recent information when they need it,
Automating user account provisioning and deprovisioning to avoid missed instances or missing deadlines.
Standardizing security policies and reviews of third-party tools, both in how reviews are conducted and at what intervals, to ensure consistency in the review process.
Of course, the right data security partner can make a world of difference.
Bitwarden Password Management Solutions
Bitwarden provides solutions to secure your business. Learn more about the solutions below.
Bitwarden Password Manager
The Fall 2023 G2 Enterprise Grid report positioned Bitwarden as the No. 1 enterprise password manager for the second consecutive quarter. G2, the world’s largest and most trusted software marketplace, ranks software products based on user reviews from its extensive community. Reviewers said they were drawn to Bitwarden for enterprise password management because of its:
Seamless combination of highly secure, enterprise-grade features
Easy to use, straightforward interface
Exceptional business value
Robust set of capabilities, such as SCIM support, widely compatible SSO integrations, and direct encrypted data sharing
They also noted that Bitwarden is the best open-source password manager. This means it’s supported by a vibrant global community of dedicated users, fostering innovation and ensuring Bitwarden remains at the forefront of password management solutions.
Case in point: a marketing agency support firm with over 3,000 associated credentials
Headquartered in Newport Beach, Calif., Golden Communications supports marketing agencies with services including website design, managed web, and digital marketing. With four locations on three continents, the growing agency serves diverse customers, from startups to Fortune 500 enterprises, and is responsible for managing and securely storing over 3,000 credentials associated with website and cloud hosting ecosystems.
To address this challenge, the company initially used LastPass for password management. The solution solved some of the company’s initial challenges but also introduced new problems:
Frustratingly long load times
Overly complex administrative and end-user functionality
Loss of valuable company troubleshooting problems using the solution across multiple devices
A pricing model that didn’t fit the needs of a growing business
Employees who had used Bitwarden for their personal accounts recommended it to the company. The migration to Bitwarden went smoothly, thanks in large part to a seamless import of records. With intuitive case management, flexible password management, and flexible administrative and organizational setup, Bitwarden has helped Golden Communications achieve greater productivity with faster load times, enabling employees to focus on what matters most — their clients.
Bitwarden Secrets Manager
Bitwarden Secrets Manager provides end-to-end encrypted secrets management for development, DevOps, and IT teams. It allows companies of any size to centrally manage secrets across the development lifecycle, securely stores secrets associated with multiple infrastructures and applications, and automates managed secrets into workflows from one centralized location.
Companies choose Bitwarden Secrets Manager for its:
Ability to help teams boost productivity and collaborate securely
Safeguard privileged credentials at scale
Provide open source codebase and other features for added developer flexibility
Quick and easy deployment
Case in point: an Oracle Retail implementation & support partner
OLR Retails has been an Oracle business partner for over 20 years. “The fact Bitwarden is open source and publishes the results of its third-party security audits gives me confidence I can trust them with my secrets," says CTO Darren Beck.
Case in point: a growing provider of outsourced IT
Operating in three Eastern U.S. cities, Complete Network is a recognized leader for outsourced IT services to small and midsize businesses. "I adopted Bitwarden Secrets Manager because I like the idea of having secrets in a secure place where I can retrieve them later," says Senior Systems Engineer John Duprey.
Case in point: a Belgium medical imaging company
Headquartered in Ghent, Belgium, XEOS is focused on improving outcomes in surgical oncology through innovations in the performance of specimen imaging.
"Secrets Manager is an easy way to transfer secrets and provide access control around those secrets," says Software Engineer Jonathan Vervaeke.
Bitwarden Passwordless.dev
Bitwarden Passworldess.dev allows companies to easily build strong, passwordless authentication in minutes. Customers, users, and employees get smooth and secure login experiences that are free from traditional passwords. Bitwarden passkeys meanwhile offer easy-to-use, passwordless authentication and secure access, with FIDO credentials stored directly on an employee’s phone or computer.
TechCrunch, the global online publication that focuses on high tech and startup companies, said Passwordless.dev “essentially makes it easier for developers to bring WebAuthn to software with a few lines of code, reducing many of the costs and complexities involved in introducing passwordless authentication to software.”
Companies choose Bitwarden Passwordless.dev because it:
Is standards-based and phishing-resistant
Allows companies to add passkeys to existing authentication platforms
Offers centralized passkey management
Has been tested and validated by thorough, third-party security assessments
Case in point: an integration platform
Lundatech AB is an integration platform based on state-of-the-art security and availability technologies for collecting, structuring, and integrating data for real-time analysis and system interoperability. It implemented Bitwarden Passwordless.dev to improve sign-up and login experiences for customers and employees and to deploy passkey logins across internal applications for a seamless authentication flow, easy onboarding, and efficient logging into internal applications.
“Bitwarden Passwordless.dev trimmed down our development process; within an hour, we had passwordless authentication up and running,” said CTO and founder Hernrik Doverhill. “We’ve eliminated tedious password resets and complicated multifactor flows with OTP codes. Our employees save time by being able to access the internal applications they need much more quickly.”
So, where to now?
Now that you’re familiar with the realities versus the myths of AI and cybersecurity, better understand the evolving role of AI in cybersecurity, and have seen how organizations like yours can proactively safeguard sensitive data, it’s time to act.
Bitwarden empowers teams and enterprises to effortlessly facilitate secure password and secret sharing among colleagues. Bitwarden can help you reduce cybersecurity risks by implementing robust password policies for all employees and enabling monitoring of activities through audit logs. Bitwarden also seamlessly integrates with your current security tools and supports SSO and directory service integrations. With features like passwordless authentication, biometric unlock, security key support, and credential autofill, Bitwarden ensures that employees can easily access their crucial accounts and sensitive data with ease.
Have questions about Bitwarden for your Business?
Talk to a specialist >
Sources
(1) Chui, M., Roberts, R., Rodchenko, T., Singla, A., Sukharevsky, A., Yee, L., & Zurkiya, D. (2023, May 12). What every CEO should know about generative AI. McKinsey & Company. Source.
(2) Lin, B. (2023b, August 10). AI is generating security risks faster than companies can keep up. WSJ. Source.
(3) Bousquette, I. (2023, July 7). Companies are drowning in too much AI. WSJ. Source.
(4) Schneier, B. (2023, February 18). The age of AI hacking is closer than you think. WIRED. Source.
(5) Generative AI enables bad actors to create more sophisticated attacks. (2023, October 3). Abnormal. Source.
(6) Satter, R. (2023, July 20). Exclusive: AI being used for hacking and misinformation, top Canadian cyber official says. Reuters. Source.
(7) Mascellino, A. (2023b, August 23). Artificial intelligence and USBs drive 8% rise in Cyber-Attacks. Infosecurity Magazine. Source.