- Resources
- Best for businesses: The Bitwarden scalable sharing model
All password managers in the market deliver on their primary promise of generating, saving, and autofilling strong, secure passwords. Where they diverge is their approach to how passwords are shared with teammates and coworkers.
Bitwarden stands out with its scalable sharing architecture that provides a single source of truth and full organization-ownership for these shared items.
Quick view:
Whether for a project or ongoing operations, teammates will need to share credentials and other sensitive information.
Why?
Some applications and web apps, such as social media, only support a single seat
Single Sign-On doesn’t cover every online tool
Not just passwords: company credit cards, secure notes, and SSH keys need sharing too
> Without a method for secure sharing, employees will send each other credentials via chat, SMS, email, post-it notes, or even word-of-mouth.
Organizations in Bitwarden have a single vault, and the organization “owns” every item within it. All sharing is managed through the organization vault. This allows for easy, scalable sharing.
How?
All vault items must be in at least one collection (shared folder)
Admins choose how collections are managed and who has access
Logical flow for assigning items: organization vault → collections → user groups
The Bitwarden centralized architecture makes vault items a single source of truth:
✅ Update an item once and it updates everywhere
✅ Delete an item, it’s gone immediately
✅ Sharing is simple and scalable
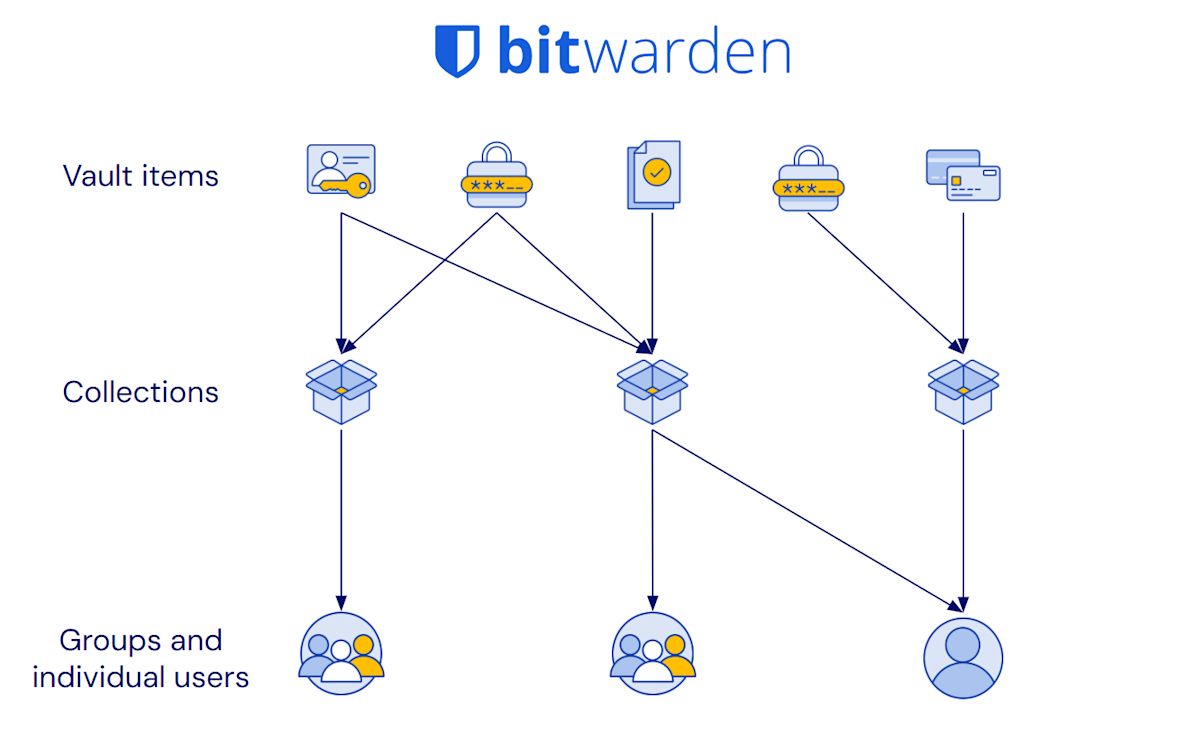
> The Bitwarden vault is organized in a logical, clear way - centralized and easy to manage.
3. Other password managers make it harder and unsafe
Not all password managers were built for scale. They were originally designed for 1:1 sharing - less useful for growing companies.
Scaling requires a workaround:
👎 Duplicate items
👎 Creating multiple shared vaults/folders
👎 Shortcuts with limited syncing
What happens when other password managers try to scale?
❌ Duplicated credentials go out of sync
❌ Admins lose visibility into what’s shared
❌ Orphaned items persist
All this results in a headache for admins and more risk.
> These shortcomings directly undermine core security principles like Least Privilege Access and Data Loss Prevention, increasing the risk of unnecessary exposure and data leakage.
Bitwarden makes sharing across teams easier and safe
✅ Reduced administrative overhead
✅ Prevent unintended over-privilege
✅ Ensuring admin oversight of organization credentials
Table of Contents
Quick View:
1. Employees need to share passwords
2. Share at scale with a centralized Bitwarden vault
3. Other password managers make it harder and unsafe
Bitwarden makes sharing across teams easier and safe
Deeper dive:
Bitwarden provides a single source of truth for sharing at scale
What other password managers try to do
The cost of going without Bitwarden
> How other solutions increase risk
> Other solutions require more IT resources
Read the Bitwarden Security Perspectives
Read more about scalable password sharing and more in the Bitwarden Security Perspectives whitepaper series.
Bitwarden Security Perspectives:
Credential lifecycle management
Deeper dive:
Centralized architecture
Bitwarden was architected with businesses in mind. Sharing is managed from a centralized vault, and only other members of the same organization can access it. Any shared item is owned directly by the organization. This offers many benefits, including clear reporting on vault security health, easy recovery of deleted items, smoother offboarding, and it allows for vault exports for backups/data portability.
TIP: Enterprise plans can enact a policy that requires all vault items, including unshared items, be stored in the centralized vault. Learn more: Enforce organization data ownership
Other password management solutions are different and were originally conceived as consumer-first products. Early on in their development, they decided to prioritize 1:1 sharing with other users that didn’t necessarily have to be teammates or coworkers. Today, they now have trouble supporting larger businesses’ sharing needs, resulting in a process that is harder to manage, introduces risk, and is not easy to understand. Their architecture creates challenges for admins that need to revoke access to specific items, adds overhead to be sure items are synced across duplicates, complicates offboarding, and makes it impossible to migrate to another service when they realize that the solution doesn’t work for them.
Bitwarden provides a single source of truth for sharing at scale
Having items in a centralized vault allows for intuitive management that makes sharing clean and easy. In Bitwarden:
All items in the organization vault are assigned to one or more collections for sharing.
Access to collections are then assigned to individual users and user groups.
Importantly: Items can belong in more than one collection, and users can belong in more than one group.
So in a common situation where two teams need access to a single item, that one item can be assigned to collections that each of those teams already have access to. There’s no need to create a duplicate item or add the collaborating team to the other team’s private space.
When that item is updated, such as in a password rotation, both teams will immediately have the new credentials. The same applies to deletion or revocation - simply go to the item and remove it from collections or delete it entirely, and access is updated for everyone. This process is clean and leaves no orphans or shortcuts to manage.
In this way, vault items are a single source of truth. All sharing, access, and item contents are in one place, the item itself.

What other password managers try to do
In order to make up for the shortfalls in architecture that make scalable sharing impossible, other password managers have concocted workarounds that end up causing headaches and increase risk.
Workaround for other password managers | Description | The problem |
|---|---|---|
Relying on duplicates | To share one item across multiple teams, the item must be duplicated and placed in each location needed. | ⚠️ Duplicates need to be manually changed whenever an update needs to be made ⚠️ When the item needs to have its access restricted or be deleted each duplicate needs to be handled separately. |
Creating separate “joint vaults” | Another way to share one item across multiple teams is to create a new vault/folder for every item that needs to be shared across teams, put the item in that shared location, then assign each team to it that needs it. | ⚠️ This massively proliferates vaults/folders, is confusing to manage, and can easily introduce errors and accidental access. |
Using “shortcuts” | Some solutions allow users to create shortcuts to items that offer limited syncing in other locations. | ⚠️ These shortcuts can be hidden away from admin oversight and aren’t deleted when the original item is deleted, opening up opportunities for credential misuse and over-privilege. |
Each of these methods are poor substitutes for an architecture that was designed for centralized ownership and scalable sharing.
The cost of going without Bitwarden
If you don’t have a scalable sharing solution like Bitwarden, as you grow you are exposing your business to additional risk while also adding to the workload of your IT team. These have real impacts to your business operations and costs.
How other solutions increase risk
Unmanaged loose ends after sharing increase chances of breached credentials and costly remediation
Unintended over-privilege leads to potential credential misuse
Credentials that lose oversight may be compromised without notice
Other solutions require more IT resources
Implementing sharing workarounds means more administrator overhead required
Extra work pulls IT bandwidth from other projects
Additional staffing up may be needed for more admins or help desk support
Try it for yourself!
When evaluating proofs of concept, check for these important attributes:
Are shared items in a vault owned by the company, or by the user?
Can one item be placed in multiple locations?
What happens when that item is updated?
Can an admin remove an item from sharing?
How can an admin recover a deleted item?